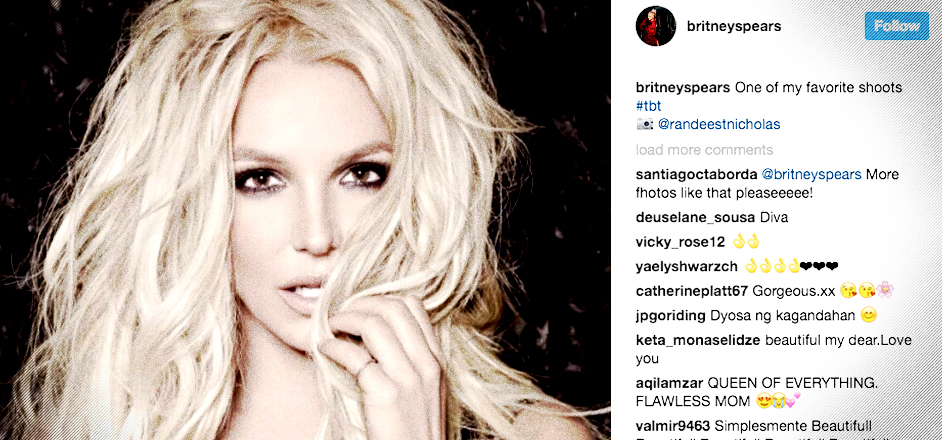
Of the 16.9 million people subscribed to Britney Spears’ Instagram, at least one of them is up to no god damn good. Recently it was found that Russian hackers are hanging out on Britney Spears’ Instagram, and not just any Russian hacking group either. It's Turla, a collective of sophisticated hackers with ties to the Russian government.
The ESET security community was the first to notice something amiss; as they seemed to be the only ones not distracted by the black honeycomb photoshoot. What did they find? Of the thousands of comments on the picture, there’s one oddball that stands out. It reads “#2hot make loved to her, uupss #Hot #X.”

Any cursory glance would quickly dismiss it as a Google translate gone horribly, horribly wrong. So, what does it mean?
Well, Turla specializes in attacking foreign states to further Russian policy, whatever that is at the time: maybe destabilizing Western governments for the purposes of laying claim to the vast rich resources in Antarctica? Hell, it’s fun to be dramatic with your speculations. The point of it truly is, to infect high-profile computers without anyone noticing.
Once the hackers have infected a computer, they need their malware to communicate with the central servers: the Command and Control system (C&C). It’s like how you still call your mother because you forget what temperature to set the oven to when reheating leftovers. Without that established communication you can’t eat; if the malware can’t contact C&C then it has no idea what to do: it’s going to starve while staring stupidly at the oven.
But setting up a means, or portal, to connect Command and Control with the malware presents a vulnerability to the hackers. It’s when they're most conspicuous. We’re talking immediately post-coital levels of conspicuous. Researchers and security experts can exploit the hacker’s portal to reverse engineer anti-malware measures. Then the jig is up. Sure is tough to make infected computers sing "I’m A Slave 4 U."
So, what does Turla do? They hide in plain sight.
The hackers are using Britney Spears’ Instagram account to post comments with links to their command center’s server. That senseless comment from above is actually a URL.
When compromised computers miss their mother-hackers they peruse Britney Spear’s Instagram in search of a link back to central command to communicate information and receive new instructions.
ESET lays out exactly how the links are encrypted:
The extension will look at each photo’s comment and will compute a custom hash value. If the hash matches 183, it will then run this regular expression on the comment in order to obtain the path of the bit.ly URL:
(?:\\u200d(?:#|@)(\\w)
Looking at the photo’s comments, there was only one for which the hash matches 183. This comment was posted on February 6, while the original photo was posted in early January. Taking the comment and running it through the regex, you get the following bit.ly URL:
Looking a bit more closely at the regular expression, we see it is looking for either @|# or the Unicode character \200d. This character is actually a non-printable character called ‘Zero Width Joiner’, normally used to separate emojis. Pasting the actual comment or looking at its source, you can see that this character precedes each character that makes the path of the bit.ly URL:
smith2155<200d>#2hot ma<200d>ke lovei<200d>d to <200d>her, <200d>uupss <200d>#Hot <200d>#X
When resolving this shortened link, it leads to static.travelclothes.org/dolR_1ert.php , which was used in the past as a watering hole C&C by the Turla crew.
The next time you decide to escape reality by browsing Britney Spears’ Instagram (we know what you’re really doing) just remember you’re not alone. Among those millions of other goggling eyes are infected computers slithering through the comments sections, trying to find a way to call home: Russia.




Leave a Reply
You must be logged in to post a comment.